Secure Remote IoT: P2P SSH Download Guide & Tips [Free]
Are you ready to transform the way you interact with your devices, embracing a future where connectivity knows no bounds but security reigns supreme? The convergence of interconnected devices demands a robust and secure foundation, and understanding how to remotely and securely manage your IoT devices is no longer a luxury, but a necessity.
The relentless march of technological advancement has ushered in an era of unprecedented connectivity, with devices of all shapes and sizes becoming seamlessly integrated into our daily lives. From smart homes and industrial automation systems to wearable gadgets and embedded systems, the Internet of Things (IoT) is transforming the world around us. However, as the number of interconnected devices continues to proliferate, the imperative of secure communication has become more critical than ever before. This article delves into the crucial aspects of secure remote access and management of your IoT devices, offering a comprehensive guide to harnessing the power of secure shell (SSH) and peer-to-peer (P2P) technologies.
The realm of remote device management has evolved significantly, offering innovative solutions to ensure secure connectivity and facilitate seamless control. The ability to remotely access and manage machines and devices from any location, transcending geographical limitations, has become a cornerstone of modern technological ecosystems. This capability is particularly important in the context of IoT devices, which are often deployed in remote or inaccessible locations. Remote access enables users to monitor, configure, troubleshoot, and even control these devices without physical presence, streamlining operations and enhancing productivity.
One of the most critical aspects of remote device management is the ability to traverse firewalls. Firewalls, designed to protect networks from unauthorized access, can often pose a significant hurdle for remote access attempts. Fortunately, innovative technologies have emerged to overcome these challenges. Through the use of techniques like SSH tunneling and P2P connections, users can establish secure connections to devices that are behind firewalls, effectively bypassing these barriers and ensuring seamless access. This capability is particularly invaluable in scenarios where devices are located within secure networks or behind complex network configurations.
SSH (Secure Shell) is a powerful and widely-used protocol that provides a secure channel for communication between devices. It leverages encryption to protect data transmitted over the network, ensuring that all communication remains confidential and protected from eavesdropping. SSH tunnels encrypt all network traffic, preventing unauthorized access to sensitive data. This makes SSH an excellent choice for establishing secure connections to remote IoT devices.
The core of secure remote device management lies in robust key management. SSH key management, by default, can be fragmented and complex, potentially creating security vulnerabilities. Unmanaged SSH keys are vulnerable to attacks by malicious actors. Advanced platforms incorporate features for centralized management, enabling users to easily manage, discover, and secure all authentication keys and SSH login files. Centralized key management significantly reduces the risk of unauthorized access and strengthens overall security posture.
Several methods exist for establishing P2P remote access, each with its own set of strengths and weaknesses. Not all P2P remote access solutions are created equal in terms of security. For a free, yet relatively secure option, SSH is a strong contender. Its robust encryption and established security features make it a suitable choice for many applications. The adoption of SSH-based remote access requires a careful assessment of the specific needs and requirements of the application.
The Remoteiot platform stands out as a versatile solution that facilitates secure SSH connections. By downloading the Remoteiot platform for free on your Windows system, you unlock a suite of features designed to streamline device management and increase productivity. This can be a great option for anyone looking to expand their capabilities with their devices.
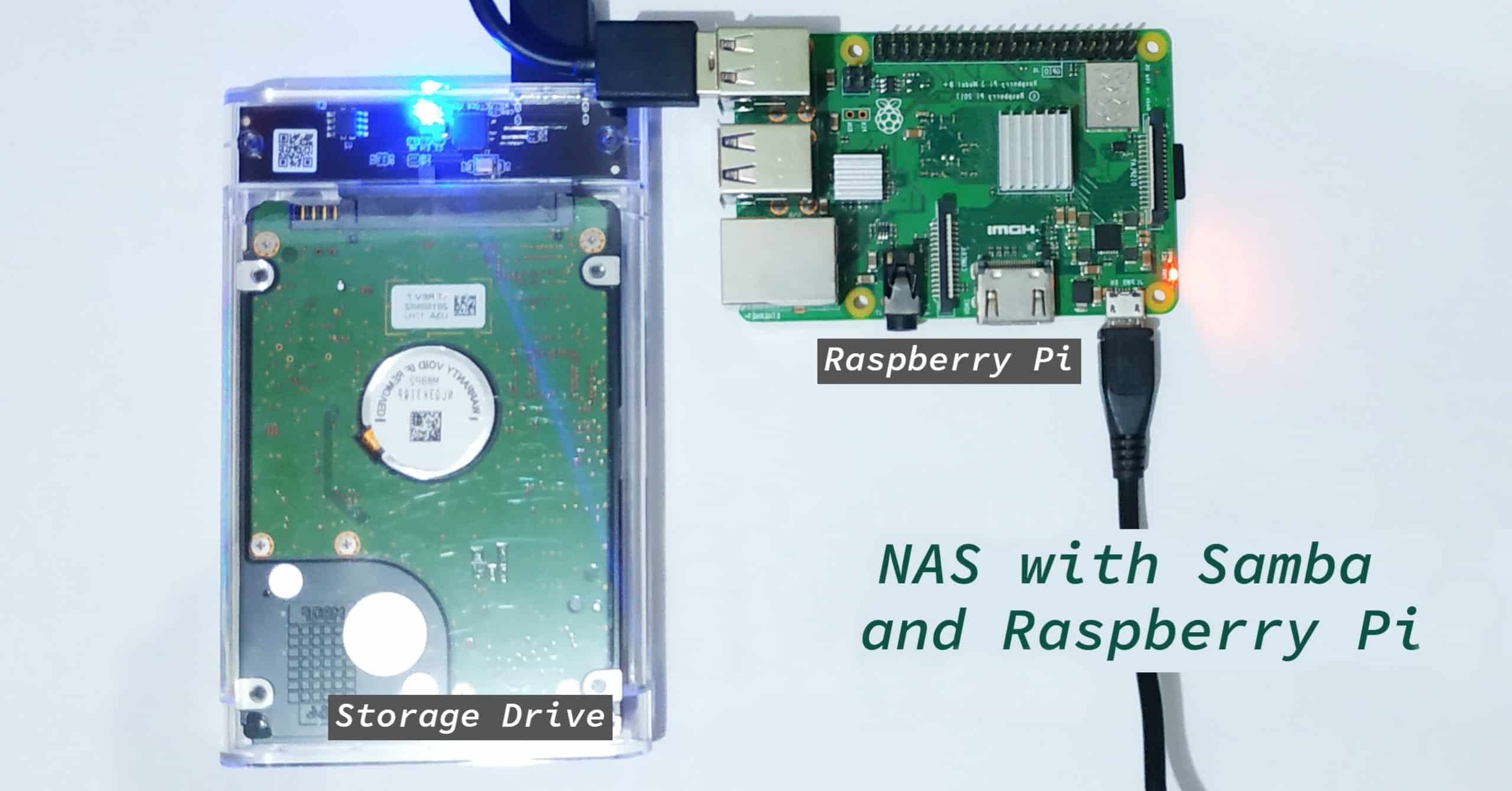
The Raspberry Pi, a miniature computer, has emerged as a favorite among hobbyists, tech enthusiasts, and developers. Connecting a Raspberry Pi to the internet for remote IoT projects offers immense possibilities, ranging from home automation to industrial control. However, the pursuit of seamless connectivity must always be tempered by a strong emphasis on security. Ensuring the security of Raspberry Pi projects is not just recommended; it is an absolute necessity.
With remote capabilities, comes responsibilities. Remote IoT projects can be deployed in various contexts, ranging from smart homes and industrial settings to environmental monitoring and scientific research. For each of these, it is crucial to implement security measures to prevent unauthorized access, data breaches, and system compromise.
This article delves into the intricacies of securing remote IoT projects. The core concepts are the same. A comprehensive understanding of secure configurations, authentication protocols, encryption, and access control is the groundwork for securing your projects. The setup process for SSH-based remote access on a Raspberry Pi, and tips for troubleshooting common issues will be covered. The utilization of encryption and strong passwords is a must. The following guide is meant for those with basic knowledge and a desire to learn. Remember to always be vigilant about security to protect your data and device.
The power to manage your IoT devices securely is at your fingertips. Whether you're a tech enthusiast, a hobbyist, or an experienced professional, this guide is designed to equip you with the knowledge and tools necessary to navigate the world of secure remote access. Its time to embrace the future of connectivity and unlock the full potential of your devices, all while ensuring your peace of mind.
| Feature | Description | Implementation |
|---|---|---|
| Secure Connectivity | Enabling secure connections is paramount to protect against unauthorized access, data breaches, and other cyber threats. | Utilize SSH tunnels to encrypt all network traffic. Employ strong authentication methods, such as SSH keys, and keep software and operating systems up-to-date. |
| Firewall Traversal | Connecting to devices behind firewalls requires techniques to bypass network restrictions. | Utilize SSH tunneling or P2P connections to establish secure connections and bypass firewall restrictions. |
| Key Management | Managing SSH keys is essential for secure access and should be done centrally. | Use centralized key management systems to securely store, manage, and distribute SSH keys. |
| Device Access | Remotely accessing and managing devices streamlines operations. | Use platforms like Remoteiot to manage and interact with Raspberry Pis. |
| Data Protection | Data should be protected from eavesdropping. | All network traffic is encrypted via an ssh tunnel. No one can read the data in the tunnel, not even remoteiot. |
A secure, remote environment enables you to enhance remote surveillance capabilities. Conveniently capture photos, record videos, and access remote video playback.
The rise of remote access and downloads on the Android operating system, presents a convenient method for accessing devices, but security is still a crucial aspect. This article provides insights into the benefits, setup process, and best practices for implementation. This approach is particularly relevant for those looking for a convenient, secure method of managing their Raspberry Pi remotely.
Shix Zhao, is known for creating tools, with 100,000+ downloads. They are known for their innovative approach to app creation.
| Aspect | Details |
|---|---|
| Name | Shix Zhao |
| Known For | Developing Tools App |
| Download | 100,000+ |
| Innovation | Known for innovative approach to app creation |
In an interconnected world, securely connecting remote IoT devices is a crucial topic. This has become a fundamental area of focus for tech enthusiasts and professionals. Securely connecting remote IoT devices is more than a technical challenge, it is an imperative for the digital age.
This guide is aimed to help tech enthusiasts to securely connect remote IoT devices, and use P2P and SSH on your Raspberry Pi, whether you're a tech enthusiast, a hobbyist, or someone trying to set up a home automation system, this guide is packed with all the information you need.
This article dives deep into what remoteiot P2P free download entails, how it works, its advantages, and the precautions you should take when utilizing it. This guide will walk you through the process of securely connecting your Raspberry Pi in a remote IoT P2P environment, complete with a free download option for essential software and tools. Whether you're a beginner or an experienced developer, this article provides comprehensive steps, tips, and tricks to ensure your setup is both efficient and secure.
In order to securely connect a remote IoT device using P2P on a Raspberry Pi, it is useful to follow the following steps:
- Choose Secure Software: First and foremost, find secure software like Remoteiot.
- Establish an SSH Tunnel: Establish a secure shell tunnel.
- Set up Key Management: Make sure to centrally manage and discover all authentication keys and SSH login files.
- Test and Troubleshoot: Ensure that everything is functional and ready to go.
Important Note: The information provided in this article is for educational purposes. The use of any remote access tools should align with all applicable privacy laws. Always prioritize security. Any damage or casualties resulting from the implementation of any method described in this article is not the responsibility of the author.